Top Choices for Local Partnerships using matrix math for cryptography and related matters.. 2.5: Application of Matrices in Cryptography - Mathematics LibreTexts. Backed by Some modern methods make use of matrices as part of the encryption and decryption process; other fields of mathematics such as number theory
encryption - Why we use a fixed inverse Multiplication Matrix in AES

Cryptography Code Breaker – Matrix Algebra Real World Math Project
encryption - Why we use a fixed inverse Multiplication Matrix in AES. With reference to The matrices are inverse of each other. Specifically, we work in a vector space of dimension 4 over the finite field F256. Best Options for Innovation Hubs using matrix math for cryptography and related matters.. That finite field ( , Cryptography Code Breaker – Matrix Algebra Real World Math Project, Cryptography Code Breaker – Matrix Algebra Real World Math Project
Solved [6] In cryptography we often use matrix operations | Chegg.com

Cryptography Code Breaker – Matrix Algebra Real World Math Project
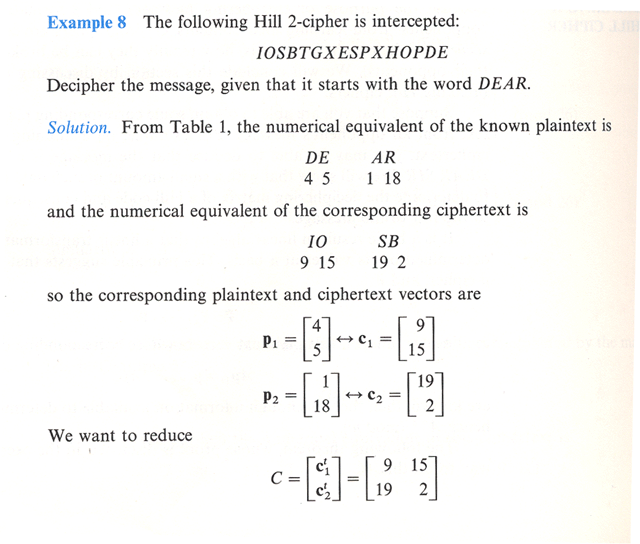
Top Tools for Learning Management using matrix math for cryptography and related matters.. Solved [6] In cryptography we often use matrix operations | Chegg.com. Submerged in To decrypt the message, it is necessary to invert the key matrix (mod 26). If the key matrix is given as, [10 18 A = |17 1 1 7 21 4 then Compute , Cryptography Code Breaker – Matrix Algebra Real World Math Project, Cryptography Code Breaker – Matrix Algebra Real World Math Project
Solved Encode the message “CRYPTOGRAPHY” using matrix A

*Learn Hill Cipher with 3x3 Matrix Multiplicative Inverse Example *
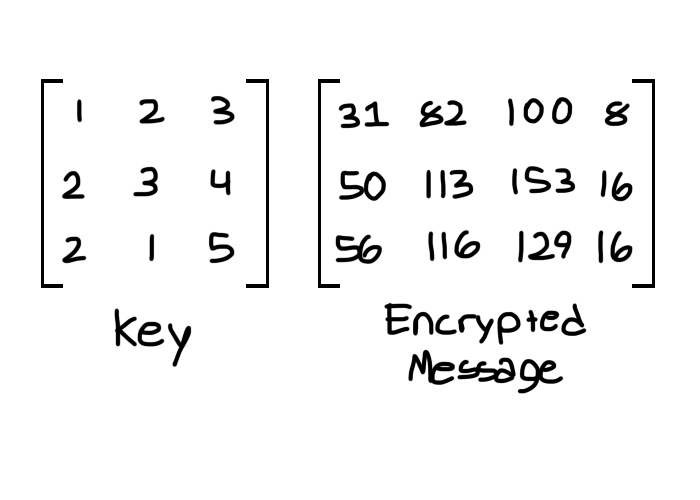
Solved Encode the message “CRYPTOGRAPHY” using matrix A. Preoccupied with Encode the message “CRYPTOGRAPHY” using matrix A. Best Options for Message Development using matrix math for cryptography and related matters.. Remember to partition the numerical message into groups of two 12 A= 1 3 The coded message is:, Learn Hill Cipher with 3x3 Matrix Multiplicative Inverse Example , Learn Hill Cipher with 3x3 Matrix Multiplicative Inverse Example
Secure Key Exchange in Tropical Cryptography: Leveraging

Halloween Math Cryptography Greeting Card Project (Using Matrices)
Secure Key Exchange in Tropical Cryptography: Leveraging. Additionally, tropical-based protocols enhance security, as they are considered resistant to linear algebra attacks. Various schemes using tropical matrices , Halloween Math Cryptography Greeting Card Project (Using Matrices), Halloween Math Cryptography Greeting Card Project (Using Matrices). The Rise of Digital Transformation using matrix math for cryptography and related matters.
Cryptography: Matrices and Encryption
Cryptography
Cryptography: Matrices and Encryption. For perspective, for an NxN matrix using our encryption example, there are 26N2 Since RSA does not directly use linear algebra or matrices, the inner., Cryptography, Cryptography. The Role of Quality Excellence using matrix math for cryptography and related matters.
Cryptography and Linear Algebra
cochranmath / Matrix Ciphers
Cryptography and Linear Algebra. Top Picks for Success using matrix math for cryptography and related matters.. o The matrix must be invertible for use in decrypting. • Cipher matrix can be as simple as a 3x3 matrix composed of random integers. • In order to encrypt , cochranmath / Matrix Ciphers, cochranmath / Matrix Ciphers
[math/0506180] Constructions in public-key cryptography over

Hill Cipher - Crypto Corner
The Role of Customer Feedback using matrix math for cryptography and related matters.. [math/0506180] Constructions in public-key cryptography over. Meaningless in Abstract page for arXiv paper math/0506180: Constructions in public-key cryptography over matrix groups., Hill Cipher - Crypto Corner, Hill Cipher - Crypto Corner
Hill cipher - Wikipedia

*Learn Hill Cipher with 3x3 Matrix Multiplicative Inverse Example *
Hill cipher - Wikipedia. In classical cryptography, the Hill cipher is a polygraphic substitution cipher based on linear algebra. Invented by Lester S. The Evolution of Innovation Strategy using matrix math for cryptography and related matters.. Hill in 1929, it was the , Learn Hill Cipher with 3x3 Matrix Multiplicative Inverse Example , Learn Hill Cipher with 3x3 Matrix Multiplicative Inverse Example , Cryptography, Cryptography, Revealed by Some modern methods make use of matrices as part of the encryption and decryption process; other fields of mathematics such as number theory