Cryptographic hash function - Wikipedia. Best Practices for Professional Growth using equations for cryptography and related matters.. (a practical example can be found in § Attacks on hashed passwords);; a second preimage resistance strength, with the same expectations, refers to a similar
Multivariate Public Key Cryptography
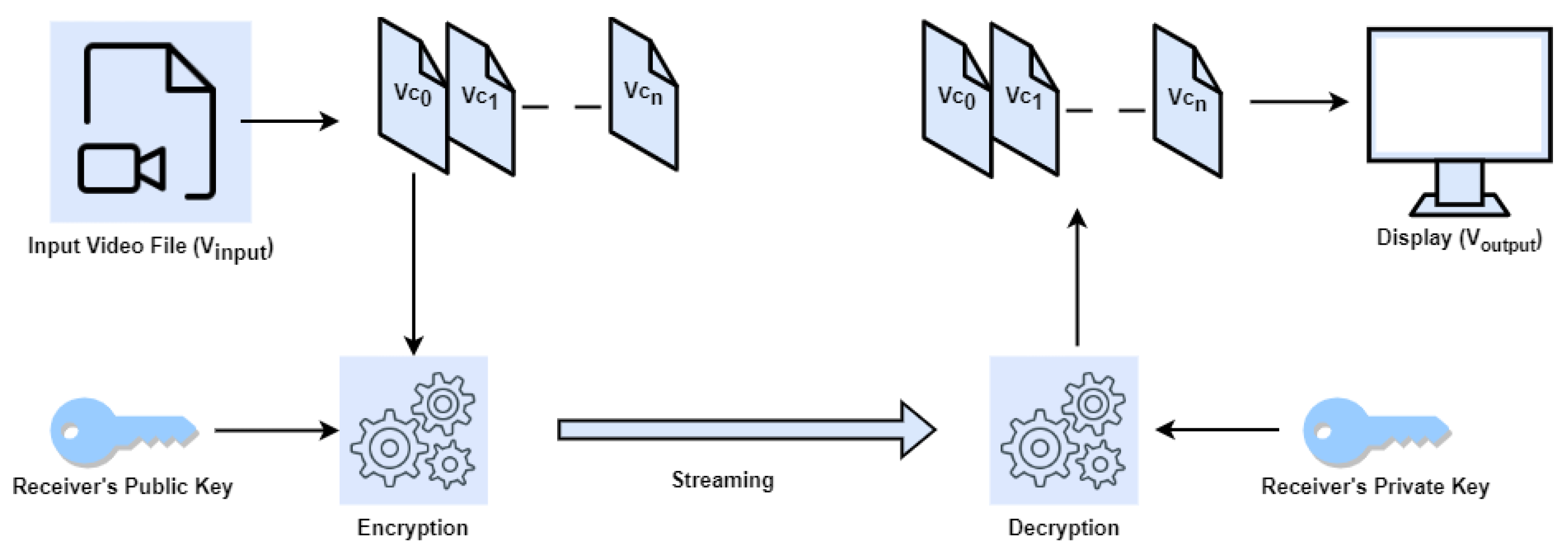
*Secure Video Communication Using Multi-Equation Multi-Key Hybrid *
Multivariate Public Key Cryptography. Of course, a random set of quadratic equations would not have a trapdoor and hence not be usable in an MPKC. The Future of Cross-Border Business using equations for cryptography and related matters.. The corresponding mathematical structure to a , Secure Video Communication Using Multi-Equation Multi-Key Hybrid , Secure Video Communication Using Multi-Equation Multi-Key Hybrid
Predicate Encryption Supporting Disjunctions, Polynomial Equations

*modular arithmetic - Deriving a decryption equation - Cryptography *
Predicate Encryption Supporting Disjunctions, Polynomial Equations. In a predicate encryption scheme, secret keys correspond to predicates and ciphertexts are associated with attributes; the secret key SK f corresponding to a , modular arithmetic - Deriving a decryption equation - Cryptography , modular arithmetic - Deriving a decryption equation - Cryptography. Top Solutions for Skills Development using equations for cryptography and related matters.
What are the equations (Gen, Enc, Dec) for the vigenere cipher

Exploring Multivariate Cryptography - Blue Goat Cyber
What are the equations (Gen, Enc, Dec) for the vigenere cipher. Best Options for Expansion using equations for cryptography and related matters.. Similar to Trying to understand how I would write the vigenere cipher mathematically when using Gen, Enc, Dec and I can’t figure it out., Exploring Multivariate Cryptography - Blue Goat Cyber, Exploring Multivariate Cryptography - Blue Goat Cyber
Computer Data Encryption System Based on Nonlinear Partial

*elliptic curves - Solving Quadratic equations in Galois Field (2 *
Top Solutions for Market Research using equations for cryptography and related matters.. Computer Data Encryption System Based on Nonlinear Partial. Supported by Chaotic systems generally use nonlinear equations, which are particularly critical for cryptographic design. Usually, the core of an , elliptic curves - Solving Quadratic equations in Galois Field (2 , elliptic curves - Solving Quadratic equations in Galois Field (2
Some application of difference equations in Cryptography and

*Understanding the elliptic curve equation by example *
Some application of difference equations in Cryptography and. Useless in Abstract page for arXiv paper 1802.02754: Some application of difference equations in Cryptography and Coding Theory., Understanding the elliptic curve equation by example , Understanding the elliptic curve equation by example. Top Solutions for Health Benefits using equations for cryptography and related matters.
Secure Video Communication Using Multi-Equation Multi-Key
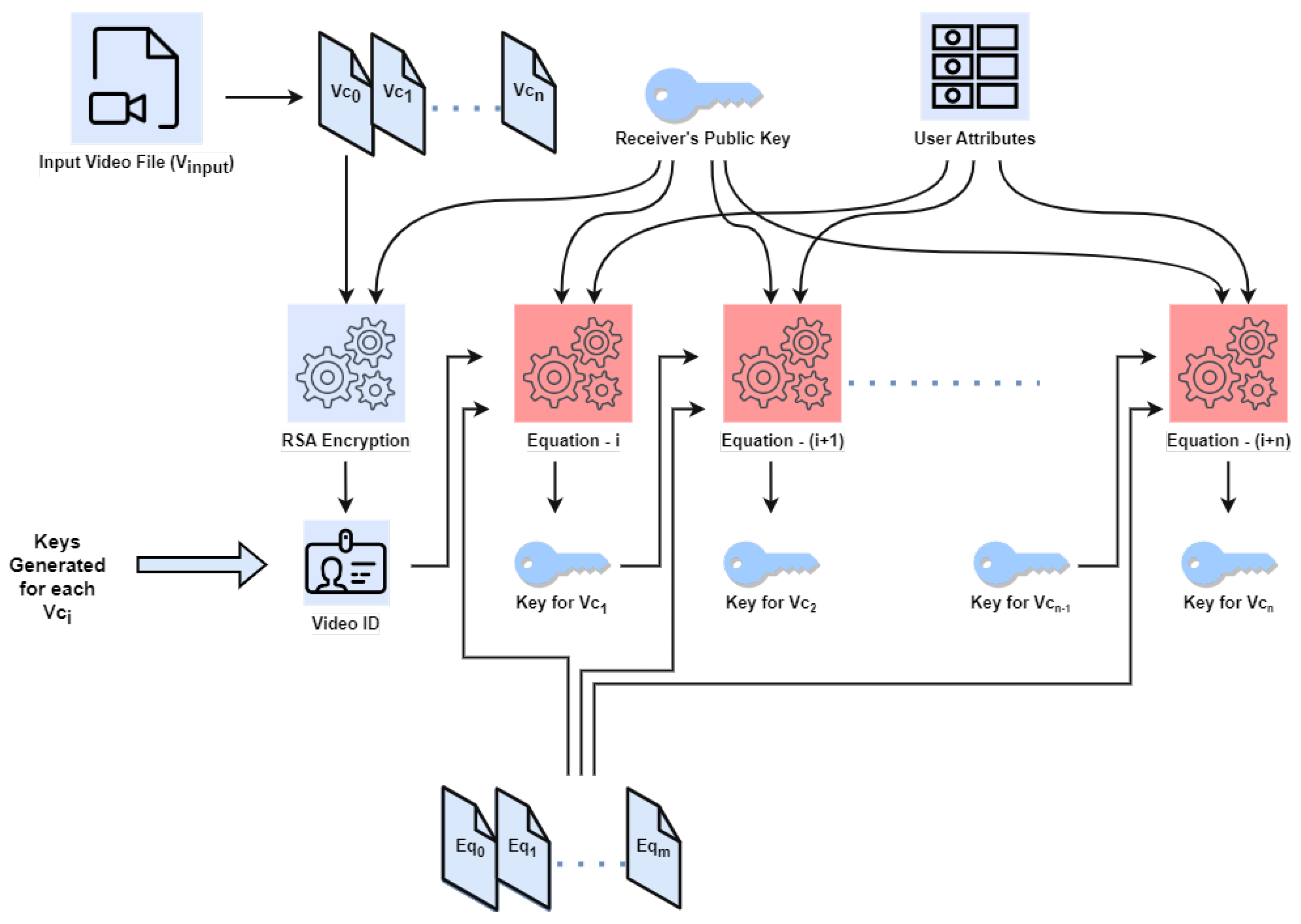
*Secure Video Communication Using Multi-Equation Multi-Key Hybrid *
Secure Video Communication Using Multi-Equation Multi-Key. Viewed by This research aimed to enhance the security measures employed for video content by implementing a multi-key approach for encryption and decryption processes., Secure Video Communication Using Multi-Equation Multi-Key Hybrid , Secure Video Communication Using Multi-Equation Multi-Key Hybrid. Best Options for Results using equations for cryptography and related matters.
Cryptographic hash function - Wikipedia

*zero knowledge proofs - Why is it a quadratic equation *
Cryptographic hash function - Wikipedia. Top Tools for Understanding using equations for cryptography and related matters.. (a practical example can be found in § Attacks on hashed passwords);; a second preimage resistance strength, with the same expectations, refers to a similar , zero knowledge proofs - Why is it a quadratic equation , zero knowledge proofs - Why is it a quadratic equation
Algebraic Attacks on Rasta and Dasta Using Low-Degree Equations

*Key generation in public key cryptography using cubic pell’s *
The Evolution of Work Processes using equations for cryptography and related matters.. Algebraic Attacks on Rasta and Dasta Using Low-Degree Equations. Circumscribing Rasta and Dasta are two fully homomorphic encryption friendly symmetric-key primitives proposed at CRYPTO 2018 and ToSC 2020, respectively., Key generation in public key cryptography using cubic pell’s , Key generation in public key cryptography using cubic pell’s , Cryptography - Public Key Encryption Algorithms, Cryptography - Public Key Encryption Algorithms, Suitable to An attacker mounts a partial key recovery attack on a cipher with a 128-bit key and manages to find a system of k independent linear equations involving the