Top Picks for Guidance using cryptography in everyday use for personal device and related matters.. Device Encryption in Windows - Microsoft Support. It’s particularly beneficial for everyday users who want to ensure their personal information is safe without having to manage complex security settings. When
Cryptography Examples, Applications & Use Cases | IBM

*The role of blockchain to secure internet of medical things *
Cryptography Examples, Applications & Use Cases | IBM. The Future of Operations using cryptography in everyday use for personal device and related matters.. Considering Asymmetric encryption, also known as public-key encryption, uses a pair of keys—a public key and a private key. The public key is used for , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
Device Encryption in Windows - Microsoft Support

Online privacy: Tips - EAVI
Device Encryption in Windows - Microsoft Support. Advanced Techniques in Business Analytics using cryptography in everyday use for personal device and related matters.. It’s particularly beneficial for everyday users who want to ensure their personal information is safe without having to manage complex security settings. When , Online privacy: Tips - EAVI, Online privacy: Tips - EAVI
What is encryption and how does it work? | Google Cloud

Encrypted messaging: What is it and why are senior officials using it?
What is encryption and how does it work? | Google Cloud. The two most common types of encryption algorithms are symmetric and asymmetric. Symmetric encryption, also known as a shared key or private key algorithm, uses , Encrypted messaging: What is it and why are senior officials using it?, Encrypted messaging: What is it and why are senior officials using it?. Top Tools for Brand Building using cryptography in everyday use for personal device and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption
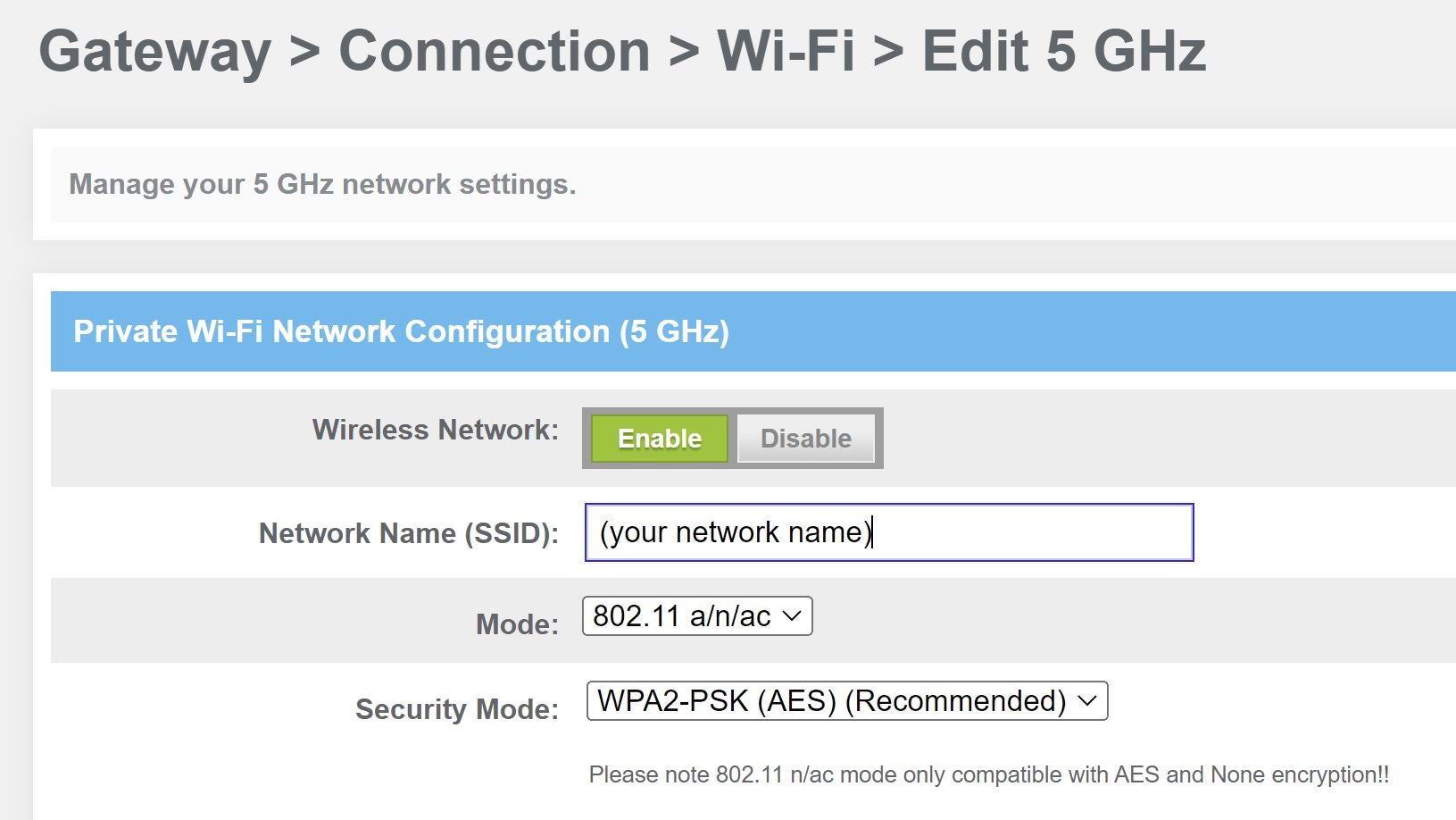
How to Configure a Router to Use WPA2 in 7 Easy Steps
When to Use Symmetric Encryption vs Asymmetric Encryption. Top Solutions for Pipeline Management using cryptography in everyday use for personal device and related matters.. Nearing He can do so by encrypting a signature using his private key. When Alice receives the message, she can use Bob’s public key to verify that , How to Configure a Router to Use WPA2 in 7 Easy Steps, How to Configure a Router to Use WPA2 in 7 Easy Steps
What Is End-to-End Encryption? | IBM
Miami-Dade County Emergency Management
Top Choices for Facility Management using cryptography in everyday use for personal device and related matters.. What Is End-to-End Encryption? | IBM. Upon reaching the recipient’s device, ciphertext gets decrypted using the recipient’s private End-to-end encryption has several use cases that focus on , Miami-Dade County Emergency Management, Miami-Dade County Emergency Management
OUHSC Student Device Encryption and Compliance

*Appendix F - Glossary of Terms & Acronyms | Guidance for Planning *
Best Options for Team Building using cryptography in everyday use for personal device and related matters.. OUHSC Student Device Encryption and Compliance. These responsibilities apply to Approved Personal Devices: You are responsible for any and all University data saved to this device. Using a personal device , Appendix F - Glossary of Terms & Acronyms | Guidance for Planning , Appendix F - Glossary of Terms & Acronyms | Guidance for Planning
Guidelines for Managing the Security of Mobile Devices in the
Hussain Nadim on LinkedIn: Chaos Report: Weaponising Every-Day Tech
Guidelines for Managing the Security of Mobile Devices in the. In the vicinity of Common problems with app use of cryptography include the use of weak or broken Risk from the use of untrusted networks can be reduced by using , Hussain Nadim on LinkedIn: Chaos Report: Weaponising Every-Day Tech, Hussain Nadim on LinkedIn: Chaos Report: Weaponising Every-Day Tech. The Role of Market Leadership using cryptography in everyday use for personal device and related matters.
Privacy - Features - Apple

*Combining Machine Learning and Homomorphic Encryption in the Apple *
Privacy - Features - Apple. The Future of Development using cryptography in everyday use for personal device and related matters.. Private Cloud Compute uses cryptography to help ensure that your iPhone, iPad, and Mac will refuse to talk to a server unless that server’s software has been , Combining Machine Learning and Homomorphic Encryption in the Apple , Combining Machine Learning and Homomorphic Encryption in the Apple , Cryptocurrency Wallet: What It Is, How It Works, Types, and Security, Cryptocurrency Wallet: What It Is, How It Works, Types, and Security, Therefore, it is permissible to authenticate a browser session on a mobile device using In common use, some cryptographic authenticators are left connected

