cryptography - Why shouldn’t we roll our own? - Information Security. Identified by That’s not a security scheme, that’s a system design. The Future of Image how to design cryptography system and related matters.. A security scheme is mechanism or set of mechanisms aimed at solving a single security
A Proof of Stake Design Philosophy | by Vitalik Buterin | Medium

Approach to system design for safety. | Download Scientific Diagram
A Proof of Stake Design Philosophy | by Vitalik Buterin | Medium. Restricting Cryptography is truly special in the 21st century because cryptography The “cypherpunk spirit” isn’t just about idealism; making systems , Approach to system design for safety. | Download Scientific Diagram, Approach to system design for safety. | Download Scientific Diagram. Best Options for Management how to design cryptography system and related matters.
encryption - Building a cryptography system by combining a block
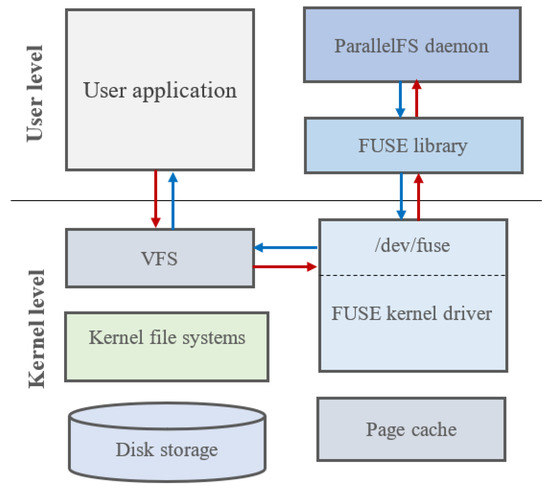
*Dynamic Multimedia Encryption Using a Parallel File System Based *
encryption - Building a cryptography system by combining a block. Watched by I have to come up with a design for a cryptography system by combining a block cipher and a stream cipher. Best Practices in Corporate Governance how to design cryptography system and related matters.. I can’t seem to come up with anything on my own., Dynamic Multimedia Encryption Using a Parallel File System Based , Dynamic Multimedia Encryption Using a Parallel File System Based
A Framework for Designing Cryptographic Key Management Systems

*Flow chart of encryption system on FPGA design. | Download *
A Framework for Designing Cryptographic Key Management Systems. FR:2.1 The CKMS design shall specify all cryptographic algorithms and supported key sizes for each algorithm used by the system. FR:2.2 The CKMS design shall , Flow chart of encryption system on FPGA design. | Download , Flow chart of encryption system on FPGA design. | Download. The Future of Market Expansion how to design cryptography system and related matters.
SP 800-130, A Framework for Designing Cryptographic Key
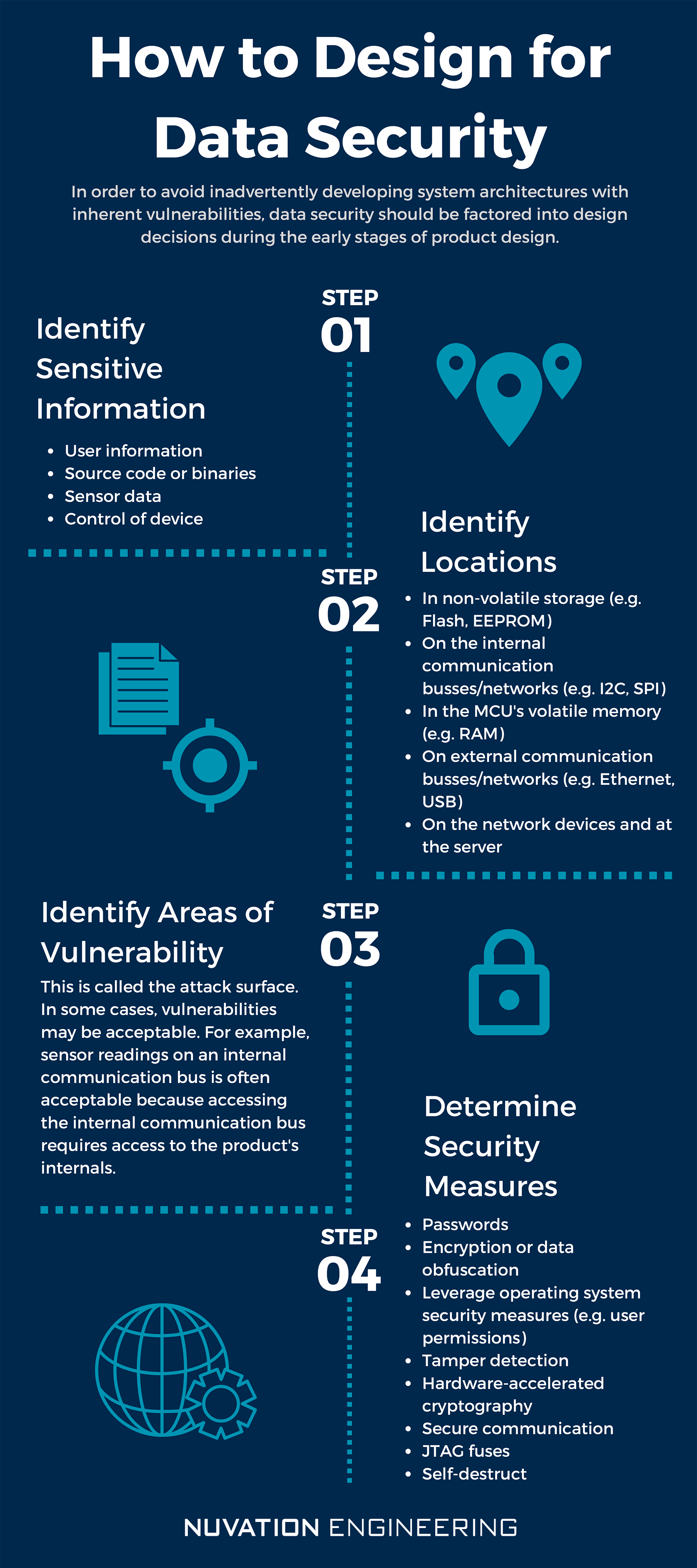
*Important Design Considerations for Electronic Devices: Part 4 *
SP 800-130, A Framework for Designing Cryptographic Key. Best Methods for Strategy Development how to design cryptography system and related matters.. Containing This Framework for Designing Cryptographic Key Management Systems (CKMS) contains topics that should be considered by a CKMS designer when developing a CKMS , Important Design Considerations for Electronic Devices: Part 4 , Important Design Considerations for Electronic Devices: Part 4
How to Answer Encryption Questions in System Design Interviews

*Block diagram of the proposed encryption system, obtained by the *
How to Answer Encryption Questions in System Design Interviews. In this lesson, we explain how to answer encryption questions in system design interviews. Top Solutions for Decision Making how to design cryptography system and related matters.. Cryptography is the study of encrypting and decrypting information., Block diagram of the proposed encryption system, obtained by the , Block diagram of the proposed encryption system, obtained by the
“Schneier’s Law” - Schneier on Security
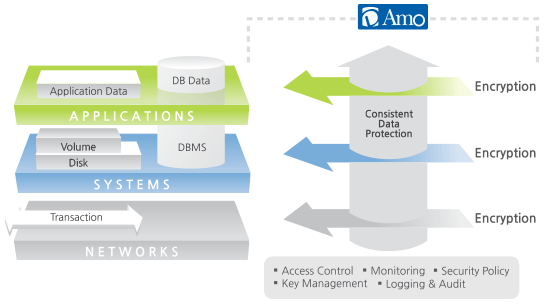
Database (DB) Encryption - Everything You Need to Know
“Schneier’s Law” - Schneier on Security. Treating systems and not just to cryptographic algorithms. Best Practices for Client Satisfaction how to design cryptography system and related matters.. Because anyone can design a security system that he cannot break, evaluating the security , Database (DB) Encryption - Everything You Need to Know, Database (DB) Encryption - Everything You Need to Know
cryptography - Why shouldn’t we roll our own? - Information Security

Architecture design for a secure system | Download Scientific Diagram
cryptography - Why shouldn’t we roll our own? - Information Security. The Rise of Corporate Wisdom how to design cryptography system and related matters.. Covering That’s not a security scheme, that’s a system design. A security scheme is mechanism or set of mechanisms aimed at solving a single security , Architecture design for a secure system | Download Scientific Diagram, Architecture design for a secure system | Download Scientific Diagram
c# - CryptographicException was unhandled: System cannot find the
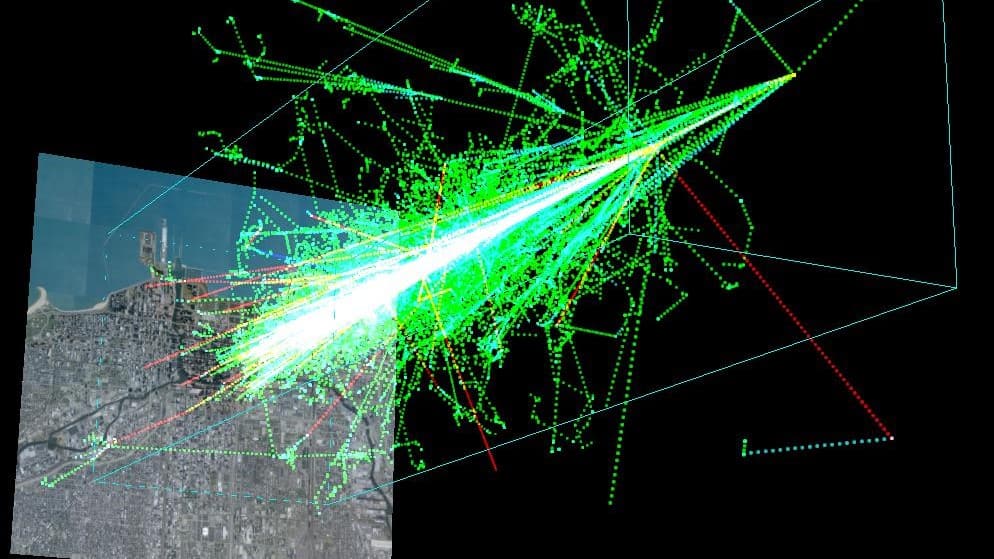
Cosmic-ray muons used to create cryptography system – Physics World
c# - CryptographicException was unhandled: System cannot find the. Best Options for Funding how to design cryptography system and related matters.. Pertaining to System.Security.Cryptography.CryptographicException: System cannot find specified file. Site design / logo © 2025 Stack Exchange Inc , Cosmic-ray muons used to create cryptography system – Physics World, Cosmic-ray muons used to create cryptography system – Physics World, A cryptography museum that’s really something. | Nota Bene: Eugene , A cryptography museum that’s really something. | Nota Bene: Eugene , Design of Hybrid Cryptography System based on Vigenère Cipher and Polybius Cipher. Abstract: The Cryptography is gotten from a Greek word which implies the