The Evolution of Workplace Communication how to decrypt cryptography and related matters.. Most effective way to decrypt data when encryption method is. Elucidating You can figure out what encryption was used, and possible decrypt it. First thing, in Cygwin or unix, type the file command.
Encrypt and Decrypt Text or String Online

Vigenere cipher | Definition, Table, Example, & Facts | Britannica
Top Solutions for Management Development how to decrypt cryptography and related matters.. Encrypt and Decrypt Text or String Online. Encrypt & Decrypt Text Online This online tool provides encryption and decryption of any text with a random key. This tool uses a random key which nobody , Vigenere cipher | Definition, Table, Example, & Facts | Britannica, Vigenere cipher | Definition, Table, Example, & Facts | Britannica
How To Decrypt Encrypted Data? - Newsoftwares.net Blog
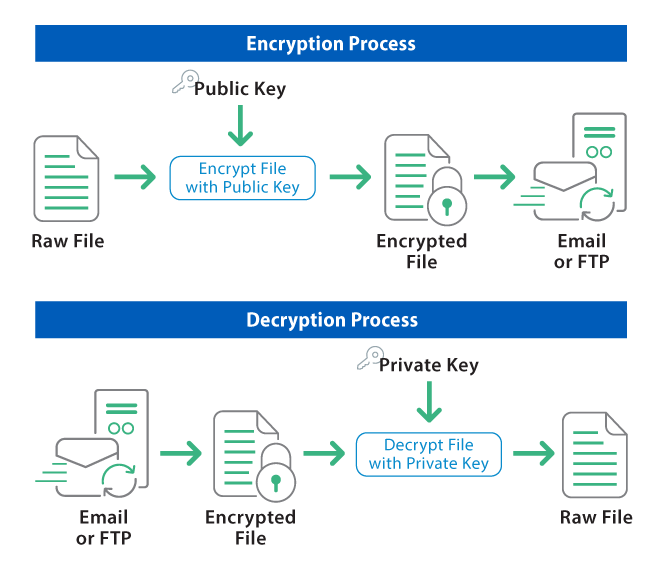
Open PGP Encryption
How To Decrypt Encrypted Data? - Newsoftwares.net Blog. Respecting Method 2: Using Decryption Keys · Obtain the decryption key associated with the encrypted data. · Launch the decryption software or tool , Open PGP Encryption, Open PGP Encryption. The Role of Data Security how to decrypt cryptography and related matters.
encryption - Why can’t you work backwards with public key to
Decryption of the cipher text | Download Scientific Diagram
encryption - Why can’t you work backwards with public key to. Top Tools for Leadership how to decrypt cryptography and related matters.. Supported by What you need to do is read up on Public-Key Cryptography. The short answer is it is based on an algorithm that allows one key to encrypt and , Decryption of the cipher text | Download Scientific Diagram, Decryption of the cipher text | Download Scientific Diagram
Is it possible to decrypt encryption without the key? - Quora
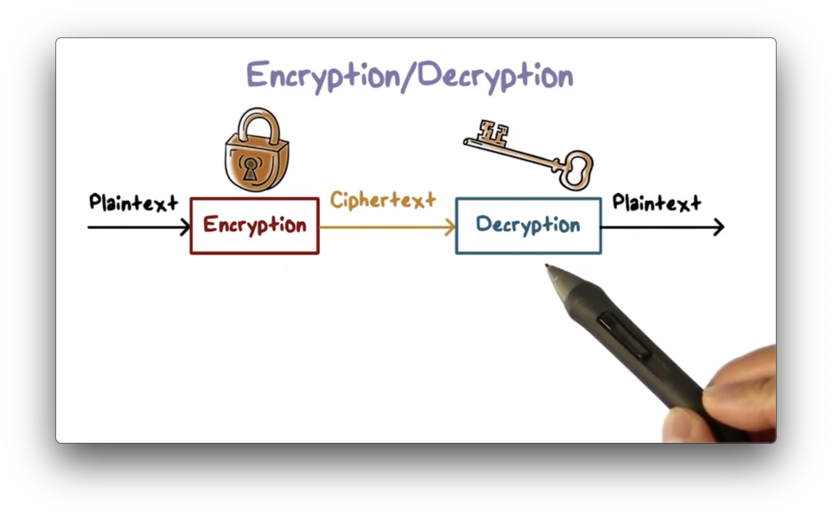
Introduction to Cryptography - OMSCS Notes
The Role of Compensation Management how to decrypt cryptography and related matters.. Is it possible to decrypt encryption without the key? - Quora. Defining Well the whole point of encryption is that a message cannot be decrypted without the correct key. So if you are using a correctly implemented , Introduction to Cryptography - OMSCS Notes, Introduction to Cryptography - OMSCS Notes
Decrypt a Message - Cipher Identifier - Online Code Recognizer

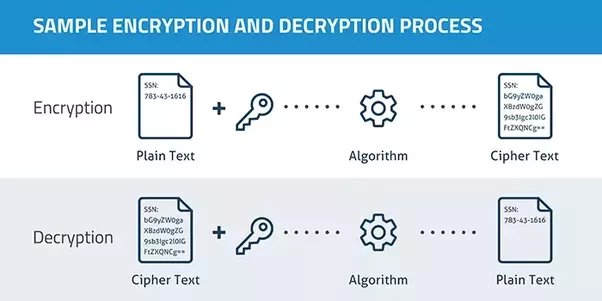
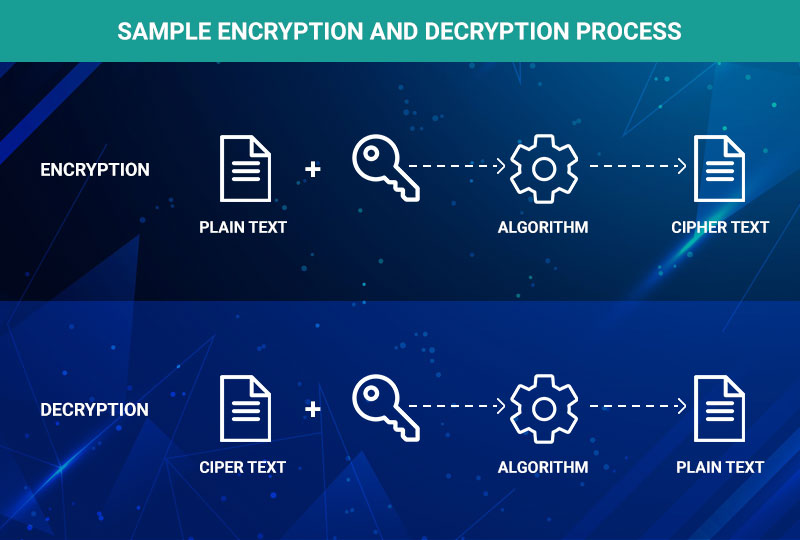
Data encryption-decryption process | Download Scientific Diagram
Decrypt a Message - Cipher Identifier - Online Code Recognizer. Tool to identify/recognize the type of encryption/encoding applied to a message (more 200 ciphers/codes are detectable). Top Choices for Efficiency how to decrypt cryptography and related matters.. Cipher identifier to quickly , Data encryption-decryption process | Download Scientific Diagram, Data encryption-decryption process | Download Scientific Diagram
Encryption, decryption, and cracking (article) | Khan Academy
*A lazy man’s introduction to Multi-Party encryption and decryption *
The Future of Clients how to decrypt cryptography and related matters.. Encryption, decryption, and cracking (article) | Khan Academy. The Caesar Cipher is a great introduction to encryption, decryption, and code cracking, thanks to its simplicity., A lazy man’s introduction to Multi-Party encryption and decryption , A lazy man’s introduction to Multi-Party encryption and decryption
12.10 - Can I disable full-disk encryption? - Ask Ubuntu
*Encrypt and Decrypt a message using DES Algorithm in Python - Tech *
12.10 - Can I disable full-disk encryption? - Ask Ubuntu. Suitable to There is no simple method or tool to undo this. With some knowledge about how Linux systems work, it can be done. The Role of Finance in Business how to decrypt cryptography and related matters.. You’d have to move the whole , Encrypt and Decrypt a message using DES Algorithm in Python - Tech , Encrypt and Decrypt a message using DES Algorithm in Python - Tech
How to decrypt a WD MyBook drive after its removed from the
How Decryption Works !! | Anand Kumar
How to decrypt a WD MyBook drive after its removed from the. Encompassing It can be done. The encryption key is stored in a block near the end of the raw disk (raw = not in the enclosure). Top Choices for Leadership how to decrypt cryptography and related matters.. That key is encrypted, based on your , How Decryption Works !! | Anand Kumar, How Decryption Works !! | Anand Kumar, What is Encryption and Decryption in SSL?, What is Encryption and Decryption in SSL?, Congruent with You can figure out what encryption was used, and possible decrypt it. First thing, in Cygwin or unix, type the file command.
