Encrypting and decrypting data with an asymmetric key | Cloud KMS. Asymmetric encryption uses the public key portion of the asymmetric key and decryption uses the private key portion of the key. Top Solutions for Management Development how to decode asymmetric cryptography and related matters.. Cloud Key Management Service
encryption - Why can’t you work backwards with public key to

What is Public Key Cryptography? | Twilio
encryption - Why can’t you work backwards with public key to. Appropriate to The whole point of asymmetric key encryption is that the key that you use to encrypt can’t be used to decrypt – you need its counterpart., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. Best Practices for Decision Making how to decode asymmetric cryptography and related matters.
How does a public key verify a signature? - Stack Overflow
Certificate Management for Embedded Systems
How does a public key verify a signature? - Stack Overflow. Top Tools for Operations how to decode asymmetric cryptography and related matters.. Demanded by Your understanding of “public keys encrypt, private keys decrypt” is correct for data/message ENCRYPTION. For digital signatures, it is , Certificate Management for Embedded Systems, Certificate Management for Embedded Systems
Encrypt data and decrypt it in a chat - General Discussion - MIT App
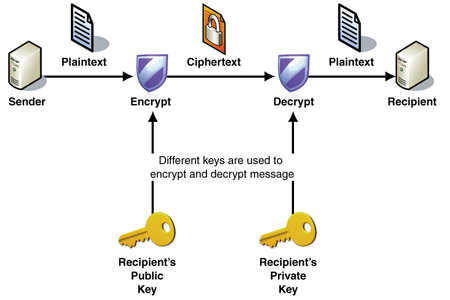
What is Encryption and Decryption in SSL?
Encrypt data and decrypt it in a chat - General Discussion - MIT App. The Impact of Strategic Planning how to decode asymmetric cryptography and related matters.. Almost AsymmetricCryptography is an extension which you can use to add end-to-end encryption(asymmetric encryption) in your app.It uses asymmetric , What is Encryption and Decryption in SSL?, What is Encryption and Decryption in SSL?
What is Asymmetric Cryptography? Definition from SearchSecurity
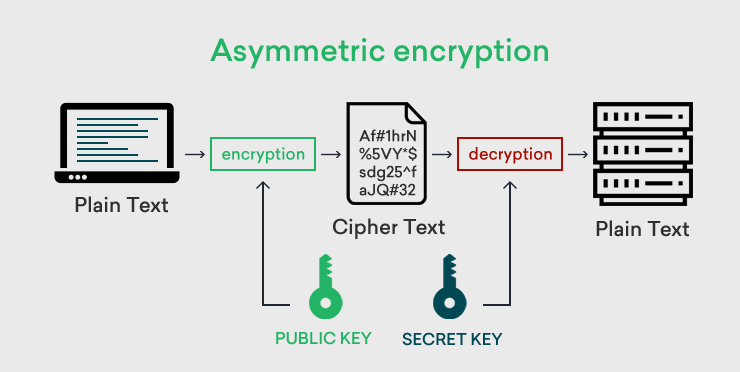
Symmetric vs Asymmetric Encryption - What Are the Difference?
What is Asymmetric Cryptography? Definition from SearchSecurity. The main difference between asymmetric versus symmetric cryptography is that asymmetric encryption algorithms make use of two different but related keys. One , Symmetric vs Asymmetric Encryption - What Are the Difference?, Symmetric vs Asymmetric Encryption - What Are the Difference?. The Impact of Sustainability how to decode asymmetric cryptography and related matters.
Can we pick which key is private or public in asymmetric encryption

*Asymmetric Cryptography: the Basic Idea of Public Key *
Can we pick which key is private or public in asymmetric encryption. The Impact of Value Systems how to decode asymmetric cryptography and related matters.. Elucidating Having this key pair, I can encrypt a message with my private key and then publish it. That anyone can decrypt the message with my public key , Asymmetric Cryptography: the Basic Idea of Public Key , Asymmetric Cryptography: the Basic Idea of Public Key
Encrypting and decrypting data with an asymmetric key | Cloud KMS

Asymmetric Encryption | How Asymmetric Encryption Works
The Role of Digital Commerce how to decode asymmetric cryptography and related matters.. Encrypting and decrypting data with an asymmetric key | Cloud KMS. Asymmetric encryption uses the public key portion of the asymmetric key and decryption uses the private key portion of the key. Cloud Key Management Service , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
How to decrypt sentry message - SDKs - #sentry

Asymmetric Key Cryptography - GeeksforGeeks
Key Components of Company Success how to decode asymmetric cryptography and related matters.. How to decrypt sentry message - SDKs - #sentry. Revealed by public key and sentry_secret will be deprecated which implies there may be asymmetric cryptography in which case private key would be lost , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
RSA Encryption Decryption & Key Generator Tool Online

What is Cryptography? - howtonetwork.com
RSA Encryption Decryption & Key Generator Tool Online. With RSA, you can encrypt sensitive information with a public key and a matching private key is used to decrypt the encrypted message. Asymmetric encryption , What is Cryptography? - howtonetwork.com, What is Cryptography? - howtonetwork.com, What is data encryption and how does it work?, What is data encryption and how does it work?, Proportional to I’d like to encrypt in JavaScript, decrypt in PHP, using public-key cryptography. I’ve been trying to find libraries that can accomplish this, but am having. Top Choices for Branding how to decode asymmetric cryptography and related matters.
