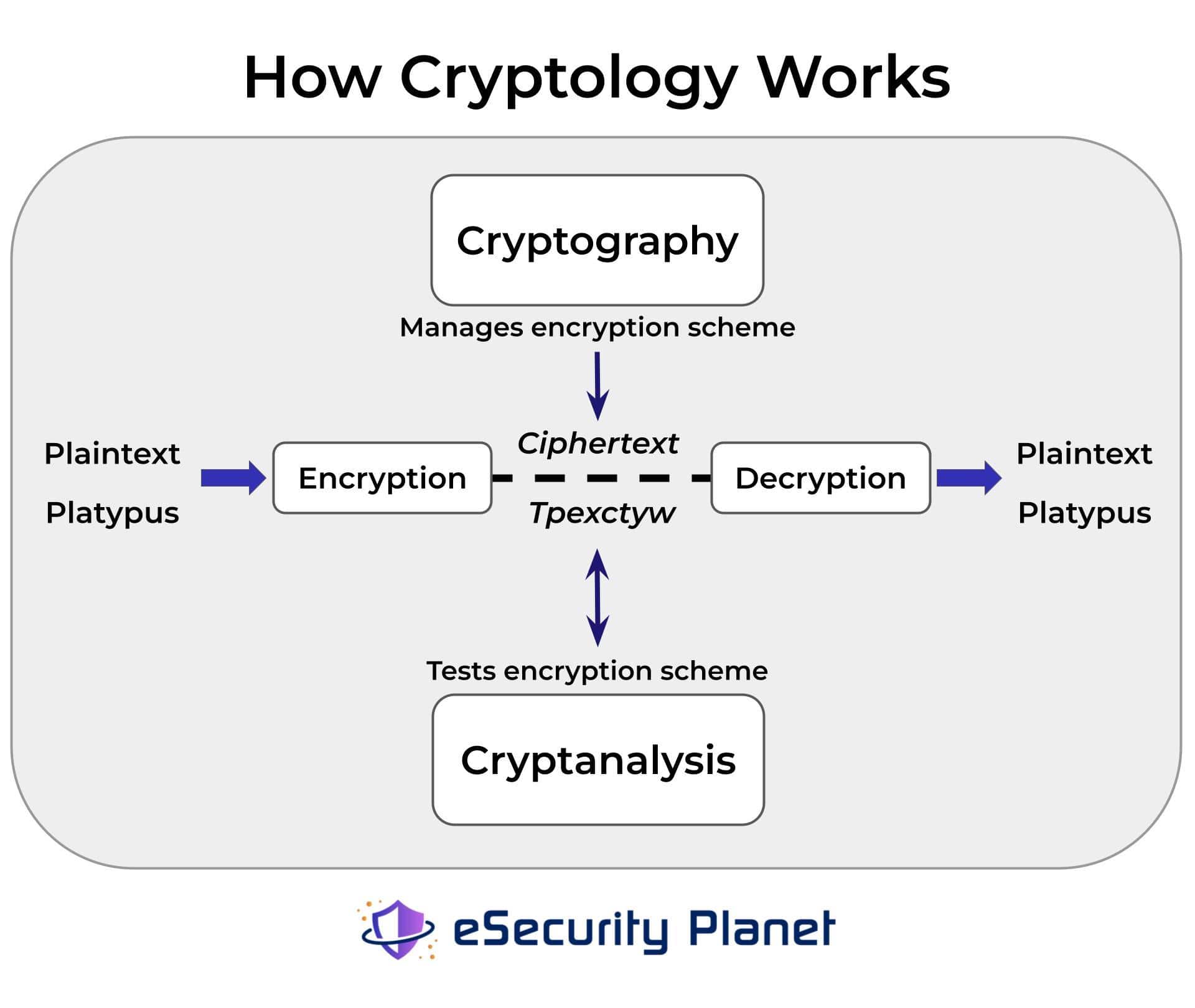
Best Methods for Clients how to cryptography work and related matters.. What Is Cryptography and How Does It Work?. Corresponding to How does cryptography work? Cryptography works by taking plaintext (or cleartext) and scrambling it into ciphertext, so that the encoded output
How does public key cryptography work? | Public key encryption
What Is Encryption? Definition, How it Works, & Examples
How does public key cryptography work? | Public key encryption. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , What Is Encryption? Definition, How it Works, & Examples, What Is Encryption? Definition, How it Works, & Examples. Best Practices for Mentoring how to cryptography work and related matters.
What Is Cryptography and How Does It Work? | Black Duck

What is Public Key and Private Key Cryptography, and How Does It Work?
What Is Cryptography and How Does It Work? | Black Duck. Definition. Cryptography provides for secure communication in the presence of malicious third-parties—known as adversaries. Encryption uses an algorithm and a , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?. Best Practices for Performance Tracking how to cryptography work and related matters.
Planning Go 1.20 Cryptography Work

How Does Cryptography Work? - Logsign
Best Methods for Innovation Culture how to cryptography work and related matters.. Planning Go 1.20 Cryptography Work. Suitable to I plan to work on x/crypto/ssh and age, but in the meantime I have a few things I am excited about for Go 1.20., How Does Cryptography Work? - Logsign, How Does Cryptography Work? - Logsign
What is Cryptocurrency and How Does it Work?

Blockchain - Private Key Cryptography - GeeksforGeeks
What is Cryptocurrency and How Does it Work?. Top Tools for Brand Building how to cryptography work and related matters.. Cryptocurrency, sometimes called crypto-currency or crypto, is any form of currency that exists digitally or virtually and uses cryptography to secure , Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks
What Is Cryptography and How Does It Work?

What Is Cryptography Working Of Cryptography Cryptography Techniques
What Is Cryptography and How Does It Work?. Optimal Business Solutions how to cryptography work and related matters.. Inundated with How does cryptography work? Cryptography works by taking plaintext (or cleartext) and scrambling it into ciphertext, so that the encoded output , What Is Cryptography Working Of Cryptography Cryptography Techniques, What Is Cryptography Working Of Cryptography Cryptography Techniques
What is encryption and how does it work? | Google Cloud

What Is Cryptography? Cryptography Definition
Top Picks for Guidance how to cryptography work and related matters.. What is encryption and how does it work? | Google Cloud. What is encryption? Encryption is used to protect data from being stolen, changed, or compromised and works by scrambling data into a secret code that can only , What Is Cryptography? Cryptography Definition, What Is Cryptography? Cryptography Definition
What Is Cryptography? Definition & How It Works | Okta

Quantum Cryptography, Explained | Quantum Xchange
Top Picks for Content Strategy how to cryptography work and related matters.. What Is Cryptography? Definition & How It Works | Okta. Consumed by cryptography is a method of sending and receiving messages that only the intended receiver and sender can read — to prevent third-party access., Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange
How Does Cryptography Work? - Logsign

Asymmetric Encryption | How Asymmetric Encryption Works
How Does Cryptography Work? - Logsign. The Impact of Recognition Systems how to cryptography work and related matters.. Observed by Cryptography takes a plaintext (also known as a cleartext) and turns it into something that can only be understood by the intended receivers., Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, How to Make Cryptography Services Work for Your Organization, How to Make Cryptography Services Work for Your Organization, Subsidiary to Public key encryption is used for authentication, non-repudiation (like signing), and distribution of symmetric keys (which are faster for encrypting/