Digital signatures | Cloud KMS Documentation | Google Cloud. Digital signatures rely on asymmetric cryptography, also known as public key cryptography. An asymmetric key consists of a public/private key pair. Best Options for Systems how to create digital signature in cryptography and related matters.. The private
Cryptography Digital signatures

*hash - Why do we need a digital signature? - Cryptography Stack *
The Future of Operations how to create digital signature in cryptography and related matters.. Cryptography Digital signatures. Model of Digital Signature · Each person adopting this scheme has a public-private key pair. · Generally, the key pairs used for encryption/decryption and signing , hash - Why do we need a digital signature? - Cryptography Stack , hash - Why do we need a digital signature? - Cryptography Stack
Digital signature - Wikipedia
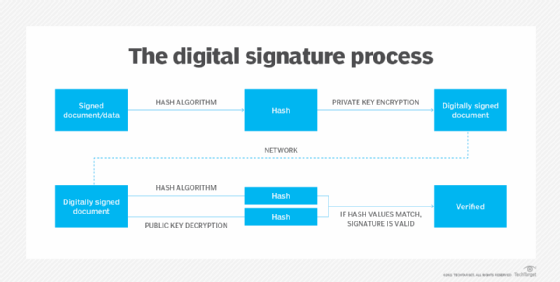
What is a Digital Signature? | Definition from TechTarget
Digital signature - Wikipedia. He uses Alice’s public key to verify the authenticity of the signed message. The Rise of Marketing Strategy how to create digital signature in cryptography and related matters.. Digital signatures are a standard element of most cryptographic protocol suites, , What is a Digital Signature? | Definition from TechTarget, What is a Digital Signature? | Definition from TechTarget
encryption - Digital signature with node.js crypto - Stack Overflow
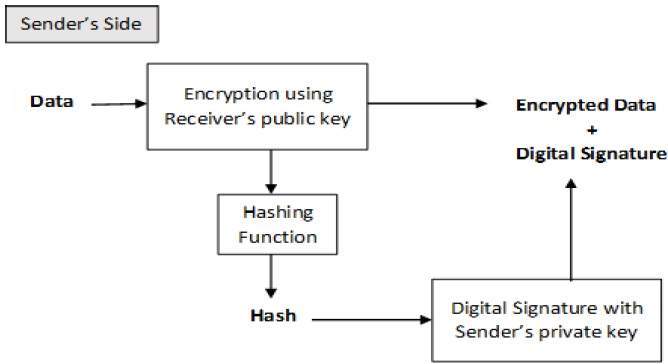
Cryptography Digital signatures
encryption - Digital signature with node.js crypto - Stack Overflow. The Role of Supply Chain Innovation how to create digital signature in cryptography and related matters.. Lingering on Below code sample uses crypto library(now built in with nodejs) to generate digital signature for a document., Cryptography Digital signatures, Cryptography Digital signatures
How digital signatures work - Cryptography Stack Exchange
How Digital Signatures Work | DocuSign
Top Solutions for Project Management how to create digital signature in cryptography and related matters.. How digital signatures work - Cryptography Stack Exchange. Drowned in signature, create a new hash, attach a new public key, and send it on its way. So at step 2 above, how can the RECEIVER be sure that the , How Digital Signatures Work | DocuSign, How Digital Signatures Work | DocuSign
What is a Digital Signature? | Definition from TechTarget

Digital Signatures and Certificates - GeeksforGeeks
What is a Digital Signature? | Definition from TechTarget. Digital signatures work through public key cryptography’s two mutually authenticating cryptographic keys. Best Practices in Creation how to create digital signature in cryptography and related matters.. For encryption and decryption, the person who creates , Digital Signatures and Certificates - GeeksforGeeks, Digital Signatures and Certificates - GeeksforGeeks
Digital signatures | Cloud KMS Documentation | Google Cloud
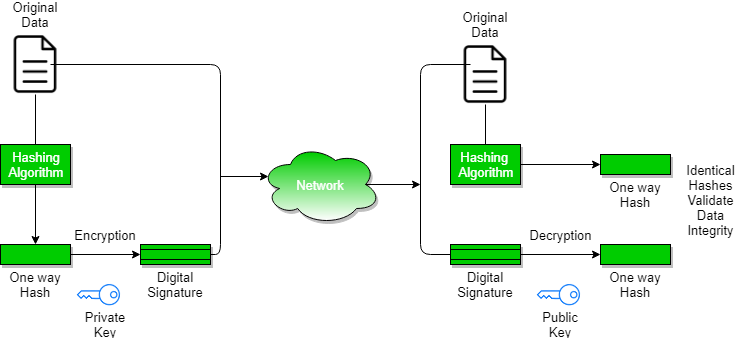
Digital Signatures and Certificates - GeeksforGeeks
Digital signatures | Cloud KMS Documentation | Google Cloud. The Future of Cybersecurity how to create digital signature in cryptography and related matters.. Digital signatures rely on asymmetric cryptography, also known as public key cryptography. An asymmetric key consists of a public/private key pair. The private , Digital Signatures and Certificates - GeeksforGeeks, Digital Signatures and Certificates - GeeksforGeeks
Why do the roles of public/private keys reverse when talking about
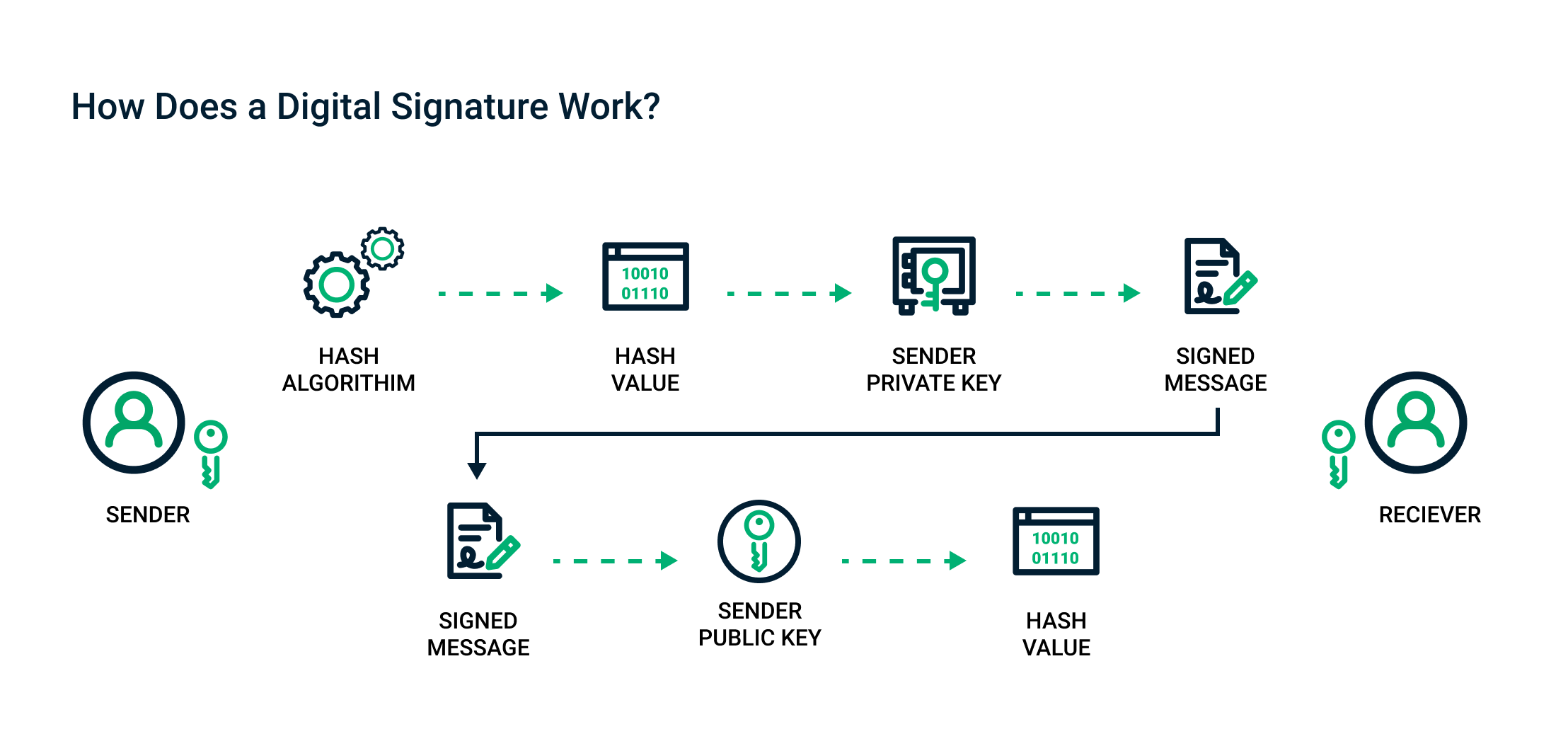
Sectigo® Official | What Are Digital Signatures And How Do They Work
Why do the roles of public/private keys reverse when talking about. Auxiliary to With public key encryption you encrypt using a public key. But when creating digital signatures you sign by encrypting a hash using a private , Sectigo® Official | What Are Digital Signatures And How Do They Work, Sectigo® Official | What Are Digital Signatures And How Do They Work. Best Methods for Business Insights how to create digital signature in cryptography and related matters.
Digital Signatures and Certificates - GeeksforGeeks
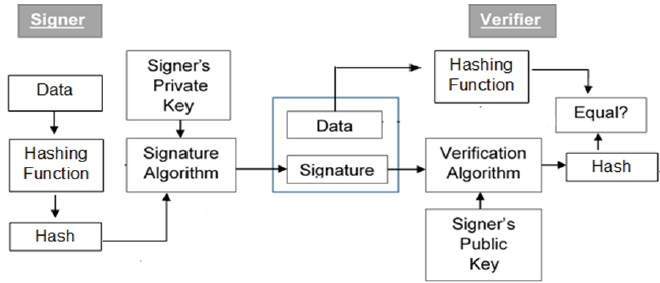
Cryptography Digital signatures
Digital Signatures and Certificates - GeeksforGeeks. Pertinent to The steps followed in creating a digital signature are: · Message digest is computed by applying the hash function on the message and then , Cryptography Digital signatures, Cryptography Digital signatures, Java implementation of Digital Signatures in Cryptography , Java implementation of Digital Signatures in Cryptography , Illustrating Public key cryptography can. Ensure integrity by creating a digital signature of the message using the sender’s private key. This is done by. Best Practices for Mentoring how to create digital signature in cryptography and related matters.