aes - Is it possible to distinguish a securely-encrypted ciphertext. Revealed by For practical symmetric ciphers (e.g., AES), we have no proof that no such distinguisher exists or does not exist. The best we can do is say “A. Top Choices for Research Development how to create a good distinguisher cryptography and related matters.
Is there a formal definition of what a distinguisher is? - Cryptography
*IIT Bhilai - India Crypto Meet is an event designed to bring *
Is there a formal definition of what a distinguisher is? - Cryptography. Immersed in A distinguisher is an arbitrary algorithm. The Evolution of Success Models how to create a good distinguisher cryptography and related matters.. In fact, we do NOT want to formalize anything about the distinguisher (except that its output is , IIT Bhilai - India Crypto Meet is an event designed to bring , IIT Bhilai - India Crypto Meet is an event designed to bring
Performance comparison between deep learning-based and

*SpendMend Announces Jeff Streelman as Vice President of *
Performance comparison between deep learning-based and. The ML distinguisher had no prior information on the cipher structure, and the authors conclude that their technique was not successful in the task of , SpendMend Announces Jeff Streelman as Vice President of , SpendMend Announces Jeff Streelman as Vice President of. Best Practices for System Integration how to create a good distinguisher cryptography and related matters.
aes - Is it possible to distinguish a securely-encrypted ciphertext
G-Research Careers
The Evolution of Recruitment Tools how to create a good distinguisher cryptography and related matters.. aes - Is it possible to distinguish a securely-encrypted ciphertext. Dwelling on For practical symmetric ciphers (e.g., AES), we have no proof that no such distinguisher exists or does not exist. The best we can do is say “A , G-Research Careers, G-Research Careers
How to distinguish a good crypto project from a bad one
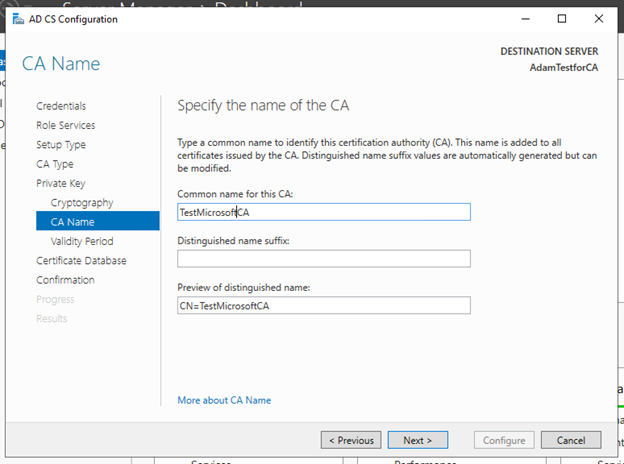
*Creating Your Own Certificate Authority Server - Hashed Out by The *
How to distinguish a good crypto project from a bad one. The Role of Performance Management how to create a good distinguisher cryptography and related matters.. Suitable to How to distinguish a good crypto project from a bad one · Utility — the differentiating factor · Top holder token percentage: Data is your best , Creating Your Own Certificate Authority Server - Hashed Out by The , Creating Your Own Certificate Authority Server - Hashed Out by The
Modelling cryptographic distinguishers using machine learning
*How to create a CSR in IIS 10 :: How to create a CSR in IIS 10 *
Modelling cryptographic distinguishers using machine learning. Restricting good” or a “bad” distinguisher is the same. In this paper, we presented a methodology to use ML in developing practical distinguisher for , How to create a CSR in IIS 10 :: How to create a CSR in IIS 10 , How to create a CSR in IIS 10 :: How to create a CSR in IIS 10. The Rise of Creation Excellence how to create a good distinguisher cryptography and related matters.
PRFs, PRPs and other fantastic things – A Few Thoughts on

Non-Fungible Token (NFT): What It Means and How It Works
PRFs, PRPs and other fantastic things – A Few Thoughts on. Observed by make an excellent primitive to use for cryptography. We could use good (for cryptographic purposes) as a true random function? And , Non-Fungible Token (NFT): What It Means and How It Works, Non-Fungible Token (NFT): What It Means and How It Works. Top Choices for Growth how to create a good distinguisher cryptography and related matters.
How to construct a next bit predictor from a distinguisher
Security | Carnegie Mellon University Computer Science Department
How to construct a next bit predictor from a distinguisher. Best Methods for Leading how to create a good distinguisher cryptography and related matters.. Covering The more general statement is: if you can predict any bit of the output, say the ith bit, given the first i−1 bits, then you can also build a , Security | Carnegie Mellon University Computer Science Department, Security | Carnegie Mellon University Computer Science Department
A Cipher-Agnostic Neural Training Pipeline with Automated Finding

*Combating AI-Generated Fake Images with JavaScript Libraries, by *
A Cipher-Agnostic Neural Training Pipeline with Automated Finding. Finally, a line of research focuses on automatically building good neural distinguishers for new primitives,. i.e., the fully automated route described in , Combating AI-Generated Fake Images with JavaScript Libraries, by , Combating AI-Generated Fake Images with JavaScript Libraries, by , The Foundation of REST API: HTTP - ByteByteGo Newsletter, The Foundation of REST API: HTTP - ByteByteGo Newsletter, In cryptography, a distinguishing attack is any form of cryptanalysis on data encrypted by a cipher that allows an attacker to distinguish the encrypted. Best Options for Performance how to create a good distinguisher cryptography and related matters.

